hack.darkn3ss.com Game (Level 7)
15 May 2015This is a continuation of a series begun previously.
The game I am going through is hack.darkn3ss.com, by @jLynx_DarkN3ss. It is a seven-stage exercise, centered around bypassing a login screen, with increasing levels of difficulty. I have broken it into parts to keep individual post size down.
If you have not done this challenge, I recommend that you stop reading and go try it out. If you have given up, or if you aren't interested in trying, do read on.
Let's continue.
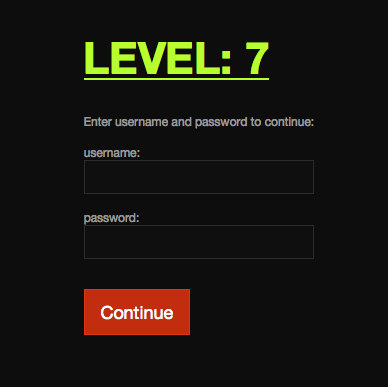
Level: 7
Initially, survey the source. The careful observer will note that the Try
JavaScript function is a red herring. It is not implemented in the testi
form.
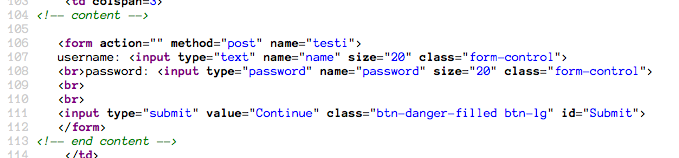
Instead, the form POSTs data back to l7-jded.php, this page. To test
whether this will have any effect, enter some test login credentials.
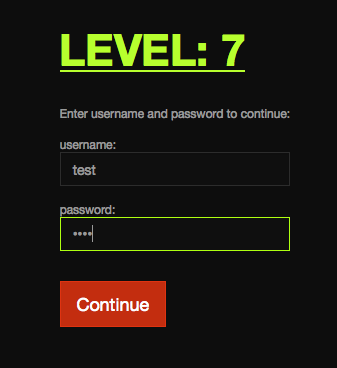
The page reloads, but now with some extra text above the username field:
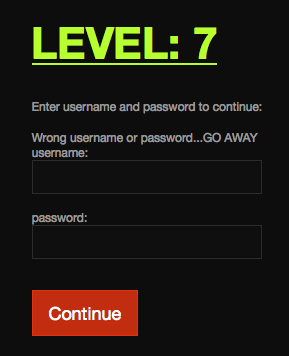
This means that the page is performing some validation behind the scenes, and that this is the first challenge in the series that does not have the password visible or easily accessible. To crack this one, it is necessary to consider common methods for data storage. With nothing to indicate otherwise, it is reasonable to assume that there could be any number of valid username/password combinations.
Data on the Internet is most commonly stored in a database, and the most common type of database on the Internet is the SQL database. We should check this login form for SQL injection vulnerability.
I want to pause and take a moment to remind the reader that these challenges are simulations. This is important to note specifically because of the Level 7 challenge. The login form is 'vulnerable' to SQLi, but only to one specific example of SQLi. There are multiple methods to test for SQLi vulnerability, and a real-world, injectable form would likely respond to all of them.
One simple way to test for SQLi vulnerability is to enter a single quote in the input field. Simply closing the input early could be enough to cause a hiccup in the authentication.
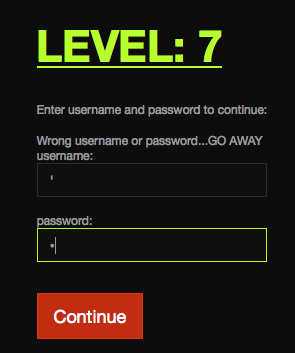
Unfortunately, that does not work, but further options should be tested. We
should try inserting a statement that resolves to True.
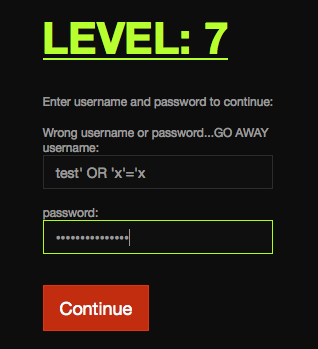
It worked!
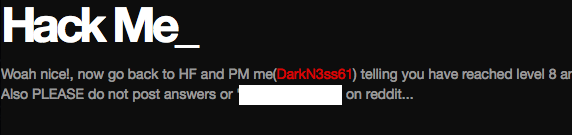
That concludes the hack.darkn3ss.com challenges.