hack.darkn3ss.com Game (Levels 4-6)
05 Feb 2015This is a continuation of a series begun previously.
The game I am going through is hack.darkn3ss.com, by @jLynx_DarkN3ss. It is a seven-stage exercise, centered around bypassing a login screen, with increasing levels of difficulty. I will be breaking it into parts to keep individual post size down and because I need to get some sleep and I only have the third level written up.
If you have not done this challenge, I recommend that you stop reading and go try it out. If you have given up, or if you aren't interested in trying, do read on.
Let's continue.
Level: 4
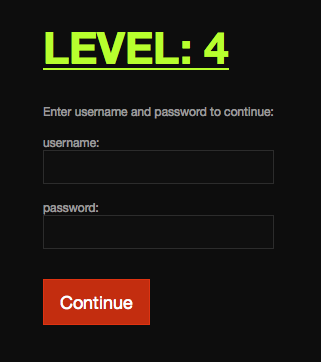
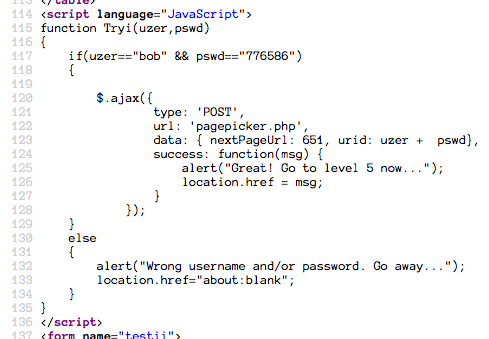
Level 4 looks pretty similar to its predecessor, Level 3. Let's jump into the source. Immediately, we can see what's going on by looking directly at the form.
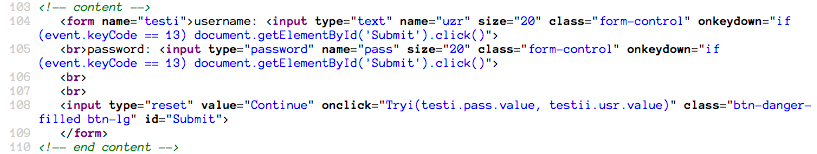
The onclick pulls from testi for one of the submitted values--the name of
this form--but for the second value it takes testii.usr.value. That's right,
it is drawing from a second form. But there was only one form visible on the
page! If we keep reading the source, we find:
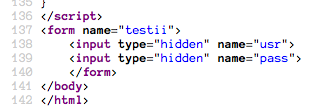
A second form, this one hidden. In order to submit this form with success, we will edit the HTML locally.
Websites are content that is delivered to your browser in the form of text files containing markup and scripting. The web browser interprets these files and displays what it is told to display. In order to read the files, they have to be downloaded onto the local machine; once these files are on the local machine, we can edit them however we want. And, because we can see how the authentication mechanism is expecting to receive input...
we can manipulate the page to match what is expected.
This can be accomplished easily with your browser's Developer Tools (any modern browser worth its salt will have this toolset available). I will be using Firefox; some of the names of tools may be specific to Firefox.
Open the Inspector, and find the submission JavaScript to get the username and password.
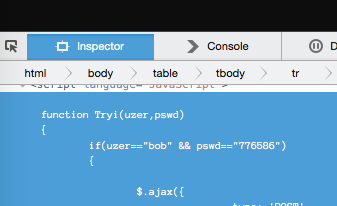
Once you have this, let's go to the hidden form and delete the hidden
attribute from the usr field. Remember, the JS takes its first input from
testi.pass and its second input from testii.usr.
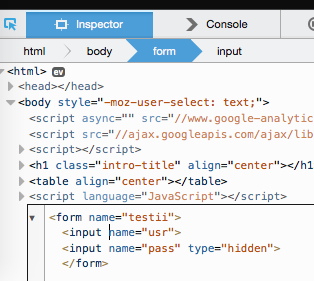
Now we can see and enter text into the once-hidden usr field. Enter the
username into testi.pass and the password into testii.usr.
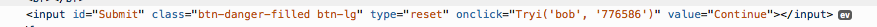
Click submit and move on to Level 5.
Alternative methods
As you might have guessed, the method I used in the above example is just one way to defeat this exercise. It's pretty simplistic. My personal favorite methods involve editing the JavaScript. One example:
Level: 5
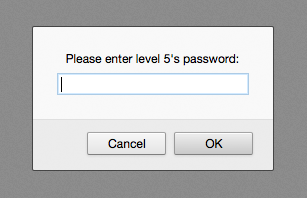
This level is different. Let's look at the source:
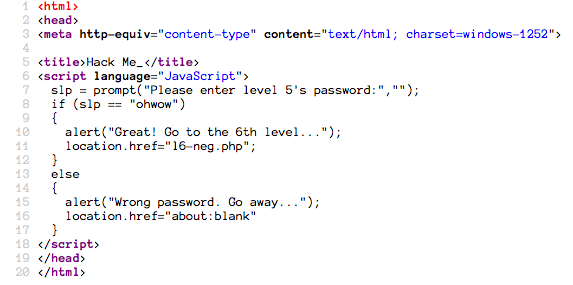
Seems too good to be true, but try it anyway.
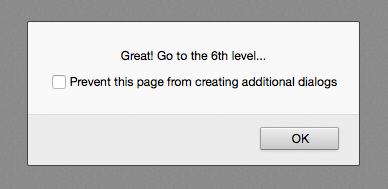
That was easy. On to Level 6!
Level: 6
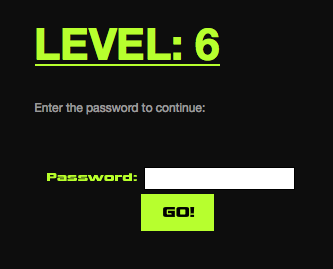
This page is using Flash to authenticate. The source immediately presents a false flag; trying the visible password yields no positive result. In order to solve this one, I needed to decode the Flash object. There are any number of resources one could use for this; I utilized showmycode.com.
I copied the link location of password.swf...
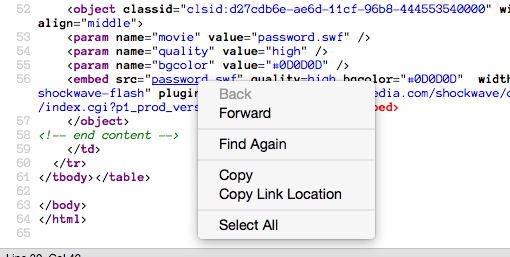
... and pasted it into the URL field at showmycode. The decoder
then presented me with the information I needed.
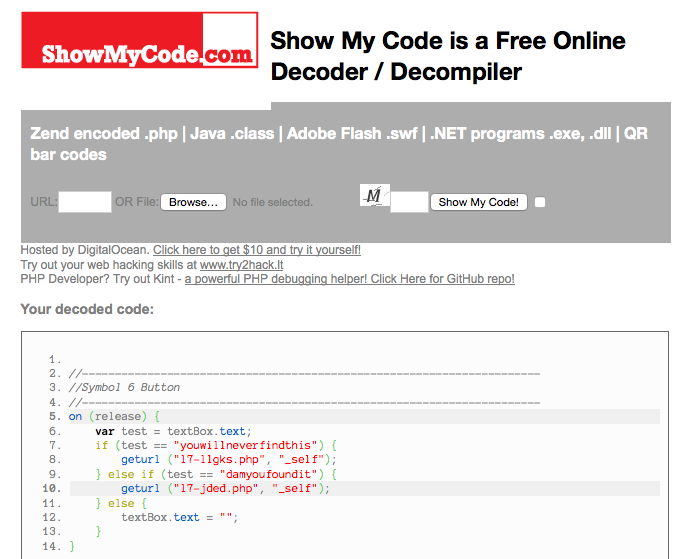
Without any way to be sure which of the strings was the password, I tried the second one first. It worked.
To be continued...
I will finish this series with my next post, which will cover the final level in this game.