hack.darkn3ss.com Game (Levels 1-3)
07 Jan 2015I'm trying to get into the practice of
- doing extra projects outside of work, and
- blogging about said projects.
In this spirit, I have decided to start with at least a couple of online hacking games/challenges that I have found entertaining. For the most part these are not terribly difficult, but fun exercises nonetheless.
The first game that I will be going through is hack.darkn3ss.com, by @jLynx_DarkN3ss. It is a seven-stage exercise, centered around bypassing a login screen, with increasing levels of difficulty. I will be breaking it into parts to keep individual post size down and because I need to get some sleep and I only have the third level written up.
If you have not done this challenge, I recommend that you stop reading and go try it out. If you have given up, or if you aren't interested in trying, do read on.
Let's get started.
Level: 1
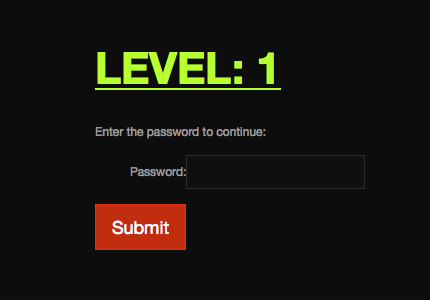
Level 1 meets us with a simple password entry screen. Submitting with a blank password or a test password yields a JavaScript alert:
Wrong password. Noob...
...and we get dumped to a blank page. However, this gives us a clue as to how this site might be validating input. Let's check the page source.
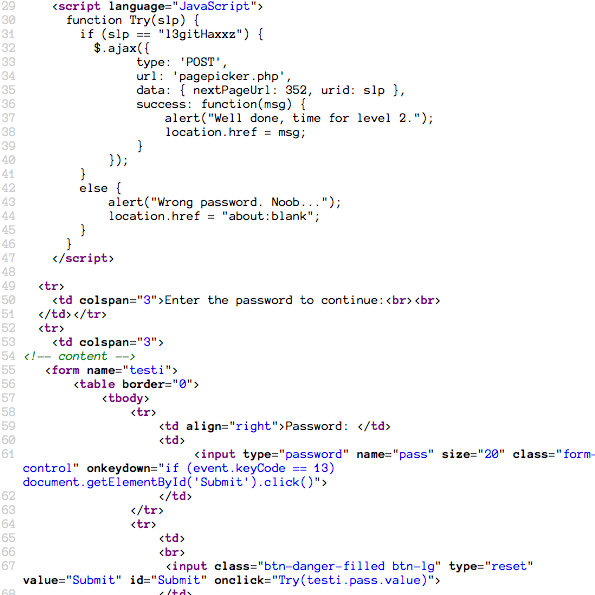
Nice. We can see a JS function being established, Try, which sadly has the
required password written in plaintext. In fact the entire situation is grim,
client-side authentication is rarely a good thing. Looking further down
the page, we can see how the function is being implemented in the testi form:
Input name pass gets handed to the function via the submit button. This
information is not important now, but I suspect it will be later. ;)
We can copy and paste in the password, click submit, and we are on to the next level.
In this level, and in some subsequent ones, we really aren't bypassing the login screen; we are just looking for the password, and the site administrator has been kind or foolish enough to leave it somewhere we could easily find it. It's the digital equivalent of hiding a sticky note under a stack of papers.
Level: 2
Very similar to Level 1, this is just another password field. The source shows another JavaScript function up top:
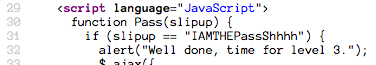
...but entering this password won't work. If we check the form, we can see
that the submit button is utilizing a JS function called Try; the function
we just looked at is called Pass. Let's find that function.
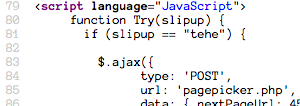
Submitting the slipup value as the password, we're done with Level 2. Just
like Level 1, the password was out where anyone could find it.
Level: 3
This is a full username and password login. Going straight to the source, we see multiple blocks of potentially useful JavaScript.
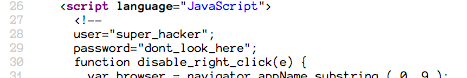
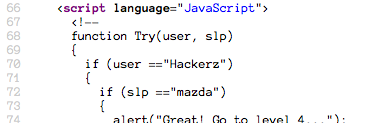
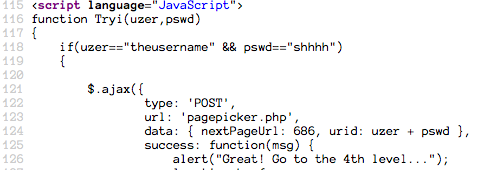
In order to tell which JS has the real password, let's check out the form.
<form name="testi">
username:
<input type="text" name="uzr" size="20" class="form-control" onkeydown="if (event.keyCode == 13) document.getElementById('Submit').click()"> <br>
password:
<input type="password" name="pass" size="20" class="form-control" onkeydown="if (event.keyCode == 13) document.getElementById('Submit').click()">
<br>
<br>
<input type="reset" value="Continue" onclick="Tryi(testi.pass.value, testi.uzr.value)" class="btn-danger-filled btn-lg" id="Submit">
</form>The third input tag defines the Submit button, and what happens when that
button is clicked. We can see that, on click, it calls a function and passes
two parameters:
onclick="Tryi(testi.pass.value, testi.uzr.value)"
Therefore, we know that the pertinent JS is the Tryi JS function.
One last thing: Notice the order the submission button's onclick passes
parameters. It sends the pass value first... which means... that the username
and password in the Tryi function are actually the password and the username.
Tricky.
Submitting the credentials in this order successfully propels us to Level 4...
... which I will cover in an upcoming post.
2015-02-05: The next post in this series is now available